I am a Researcher at the School of Software Technology, Zhejiang University  . Before joining ZJU, I worked at Huawei 2012 Lab
. Before joining ZJU, I worked at Huawei 2012 Lab  as a Senior Engineer. I received my Ph.D. degree from the Department of Computer Science and Technology at Zhejiang University.
as a Senior Engineer. I received my Ph.D. degree from the Department of Computer Science and Technology at Zhejiang University.
My research interests lie in system security, intrusion detection, and cyber threat analysis. My current work focuses on designing practical intrusion detection and attack investigation systems. I work closely with Prof. Shouling Ji, Prof. Fan Zhang from Zhejiang University and Prof. Yan Chen from Northwestern University,.
Recent research interests include:
- Intelligent yet Effcient Cyber Attack Hunting
- Automatic Penetration and Attack Planning
- Action Security for LLM Agents
Feel free to contact me if you are interested in industry-oriented security research.(招收2026级硕士生4-5名, 欢迎联系!)
🔥 News
- 📑 2026.02, Two Posters titled “Abstracting and Tracking Semantic Flow among Agents for Threat Detection” and “Reconstructing the Provenance of Android” to appear in NDSS’26/
- 📑 2026.01, Two Work-In-Progress papers, titled “Building Next-Generation Datasets for Provenance-Based Intrusion Detection” and “The Case for LLM-Enhanced Backward Tracking” accepted by PRISM’26 co-located wiht NDSS’26.
- 🧑💻 2025.12, Invited to serve as an TPC member for “GlobalCom 2026 CISS”.
- 🎉 2025.12, Awarded First Prize in the Science and Technology Progress Award by “China General Chamber of Commerce” (ranked 5/15) – “Key Technologies and Industrial Applications of AI-Driven Cybersecurity Detection.”
- 🎉 2025.12, Awarded Second Prize of the Beijing Municipal Science and Technology Progress Award (ranked 7/10) – “Key Technologies and Applications for Detection and Attribution of Highly Stealthy Cyber Threats Based on Anti-Stealth Mechanisms”.
- 🧑💻 2025.12, Invited to serve as an Early Career Editorial Board member for the journal “Digital Twins and Applications”.
- 📑 2025.11, Our paper “Actionable, Customizable, and Causality-Preserving Cyberattack Emulation with LLM-powered Symbolic Planning” is accepted by ACNS’26.
- 🏗️ 2025.11, Granted Natural Science Foundation of Ningbo (Youth Ph.D Program) as PI.
- 📑 2025.11, Our paper “Breaking the Bulkhead: Demystifying Cross-Namespace Reference Vulnerabilities in Kubernetes Operators” is accepted by NDSS’26.
- 📑 2025.10, Our paper “Towards Scalable and Interpretable Mobile App Risk Analysis via Large Language Models” is accepted by ICSE’26.
- 📑 2025.09, Our paper “Incorporating Gradients to Rules: Towards Online, Adaptive Provenance-based Intrusion Detection” is accepted by TDSC.
- 🏗️ 2025.07, Granted CCF-Tencent “Rhino-Bird” Open Research Fund as PI.
- 📑 2025.07, Our paper “Learning in Provenance-Based Intrusion Detection: A Survey” accepted by Chinese Journal of Computers.
- 📑 2025.05, Our paper “The Case for Learned Provenance-based System Behavior Baseline” is accepted by ICML’25.
- 📑 2025.04, One paper “PentestAgent: Incorporating LLM Agents to Automated Penetration Testing” is accepted by AsiaCCS’25.
- 🧑💻 2025.03, Invited to serve as an TPC member for “GlobalCom 2025 CISS”.
- 🎉 2024.09, Awarded Ningbo “YongJiang” Talent Programme (Youth Program).
- 🏗️ 2024.08, Granted National Natural Science Foundation of China (Youth Program) as PI.
- 📑 2024.08, Our paper “Incorporating Gradients to Rules: Towards Lightweight, Adaptive Provenance-based Intrusion Detection” is accepted by NDSS’25.
🛠️ Projects
- Automated Penetration Testing
- Aurora: Automated Cyberattack Emulation
- Marlin: Streaming Provenance Graph Analysis
📝 Selected Publications
Full List: Google Scholar (* Equally Contribution, # Corresponding Author)
[ArXiv]
[A3] ArXiv 2025 “Automated Penetration Testing with LLM Agents and Classical Planning”, Lingzhi Wang, Xinyi Shi, Ziyu Li, Yi Jiang, Shiyu Tan, Yuhao Jiang, Junjie Cheng, Wenyuan Chen, Xiangmin Shen, Zhenyuan Li, Yan Chen
[A2] ArXiv 2025 “AEAS: Actionable Exploit Assessment System”, Xiangmin Shen, Wenyuan Cheng, Yan Chen, Zhenyuan Li, Yuqiao Gu, Lingzhi Wang, Wencheng Zhao, Dawei Sun, Jiashui Wang
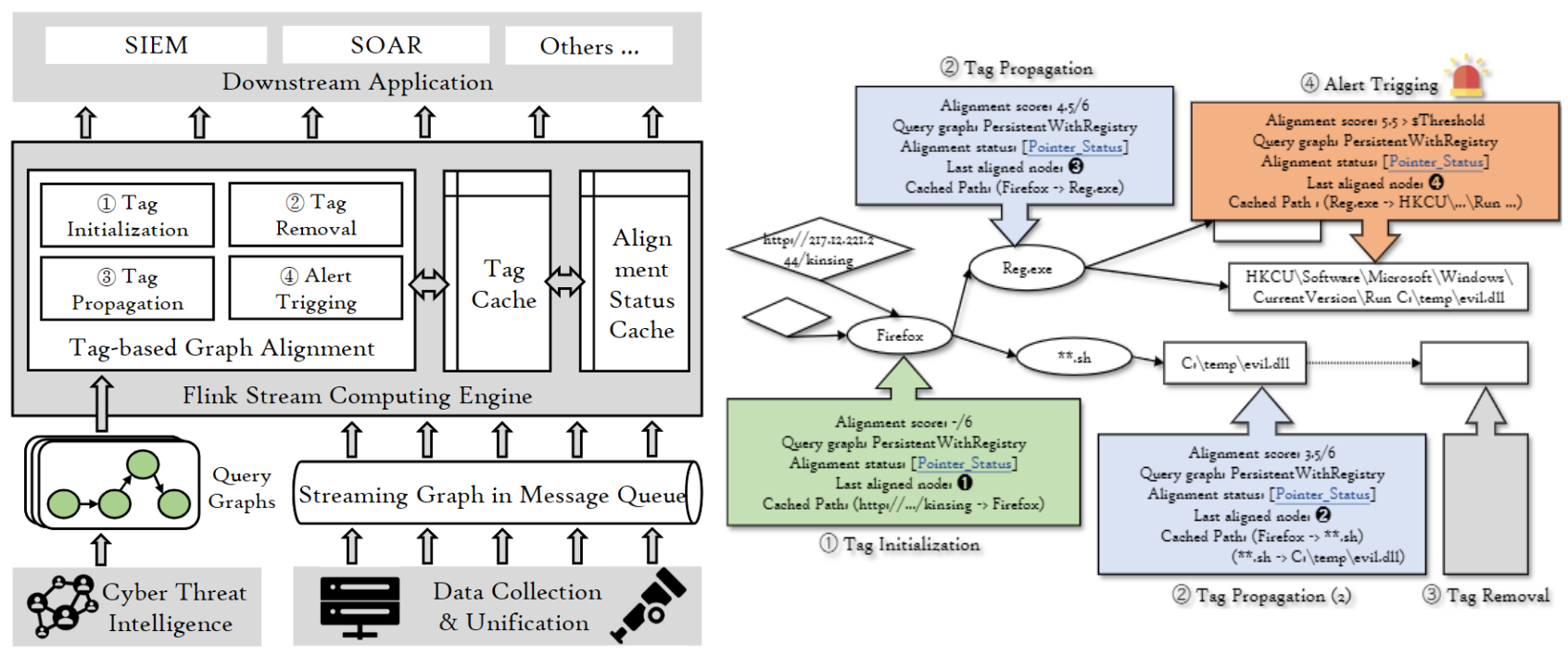
Zhenyuan Li, Yangyang Wei, Xiangmin Shen, Lingzhi Wang, Yan Chen, Haitao Xu, Shouling Ji, Fan Zhang, Liang Hou, Wenmao Liu, Xuhong Zhang, Jianwei Ying
- Marlin conceptualize real-time attack detection in streaming logs as a streaming graph alignment problem, leveraging query graphs to pinpoint critical elements in the provenance graph. Integrated into a tag propagation framework, it processes each event once, reducing redundancy and enhancing efficiency and defense against evasion.
[Conference Papers]
[C10] ACNS 2026 “Actionable, Customizable, and Causality-Preserving Cyberattack Emulation with LLM-powered Symbolic Planning”, Lingzhi Wang, Zhenyuan Li, Yi Jiang, Zhengkai Wang, Xiangmin Shen, Wei Ruan, Yan Chen
[C9] ICSE 2026 “Towards Scalable and Interpretable Mobile App Risk Analysis via Large Language Models”, Yu Yang*, Zhenyuan Li*#, Xiandong Ran, Jiahao Liu, Jiahui Wang, Bo Yu, Shouling Ji
[C8] NDSS 2026 “Breaking the Bulkhead: Demystifying Cross-Namespace Reference Vulnerabilities in Kubernetes Operators”, Andong Chen, Ziyi Guo, Zhaoxuan Jin, Zhenyuan Li#, Yan Chen
[C7] ICML 2025 “The Case for Learned Provenance-based System Behavior Baseline”, Yao Zhu*, Zhenyuan LI*#, Yangyang Wei, Shouling Ji
[C6] AsiaCCS 2025 “PentestAgent: Incorporating LLM Agents to Automated Penetration Testing”, Xiangmin Shen, Lingzhi Wang, Zhenyuan Li, Yan Chen, Wencheng Zhao, Dawei Sun, Jiashui Wang, Wei Ruan
[C5] NDSS 2025 “Incorporating Gradients to Rules: Towards Lightweight, Adaptive Provenance-based Intrusion Detection”, Lingzhi Wang, Xiangmin Shen, Weijian Li, Zhenyuan Li#, R Sekar, Han Liu, Yan Chen
[C4] INFOCOM 2025 “Understanding the Business of Online Affiliate Marketing: An Empirical Study”, Haitao Xu, Yiwen Sun, Kaleem Ullah Qasim, Shuai Hao, Wenrui Ma, Zhenyuan Li, Fan Zhang, Meng Han, Zhao Li
[C3] AsiaCCS 2024 “Decoding the MITRE Engenuity ATT&CK Enterprise Evaluation: An Analysis of EDR Performance in Real-World Environments”, Xiangmin Shen, Zhenyuan Li, Graham Burleigh, Lingzhi Wang, Yan Chen
[C2] ESORICS 2022 “AttacKG: Constructing Technique Knowledge Graph from Cyber Threat Intelligence Reports”, Zhenyuan Li, Jun Zeng, Yan Chen, Zhenkai Liang
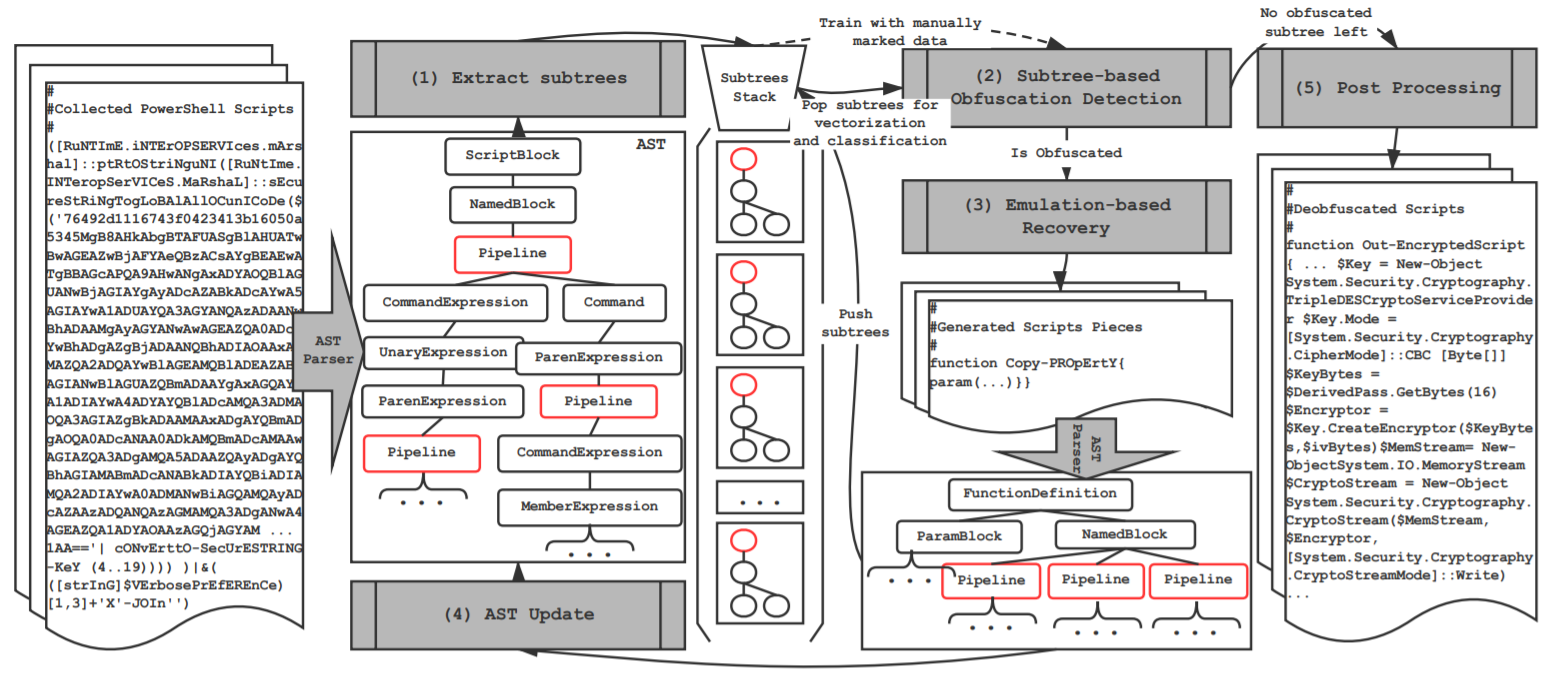
“Effective and Light-Weight Deobfuscation and Semantic-Aware Attack Detection for PowerShell Scripts”
Zhenyuan Li, Qi Alfred Chen, Chunlin Xiong, Yan Chen, Tiantian Zhu, Hai Yang
- The first effective and light-weight deobfuscation approach for PowerShell scripts. Adopted in the product of an startup security company
 .
.
[Journal Papers]
[J7] Microelectronics & Computer (in Chinese) “Analysis, Description, and Reproduction Methods for Attack Processes Driven by Large Language Models”, Jin Qian, Shiyu Tan, Libin Xu, Jun Luo, Zhenyuan Li#
[J6] TDSC 2025 “Incorporating Gradients to Rules: Towards Online, Adaptive Provenance-based Intrusion Detection”, Zhenyuan Li#, Lingzhi Wang, Zhengkai Wang, Xiangmin Shen, Haitao Xu, Yan Chen, Shouling Ji
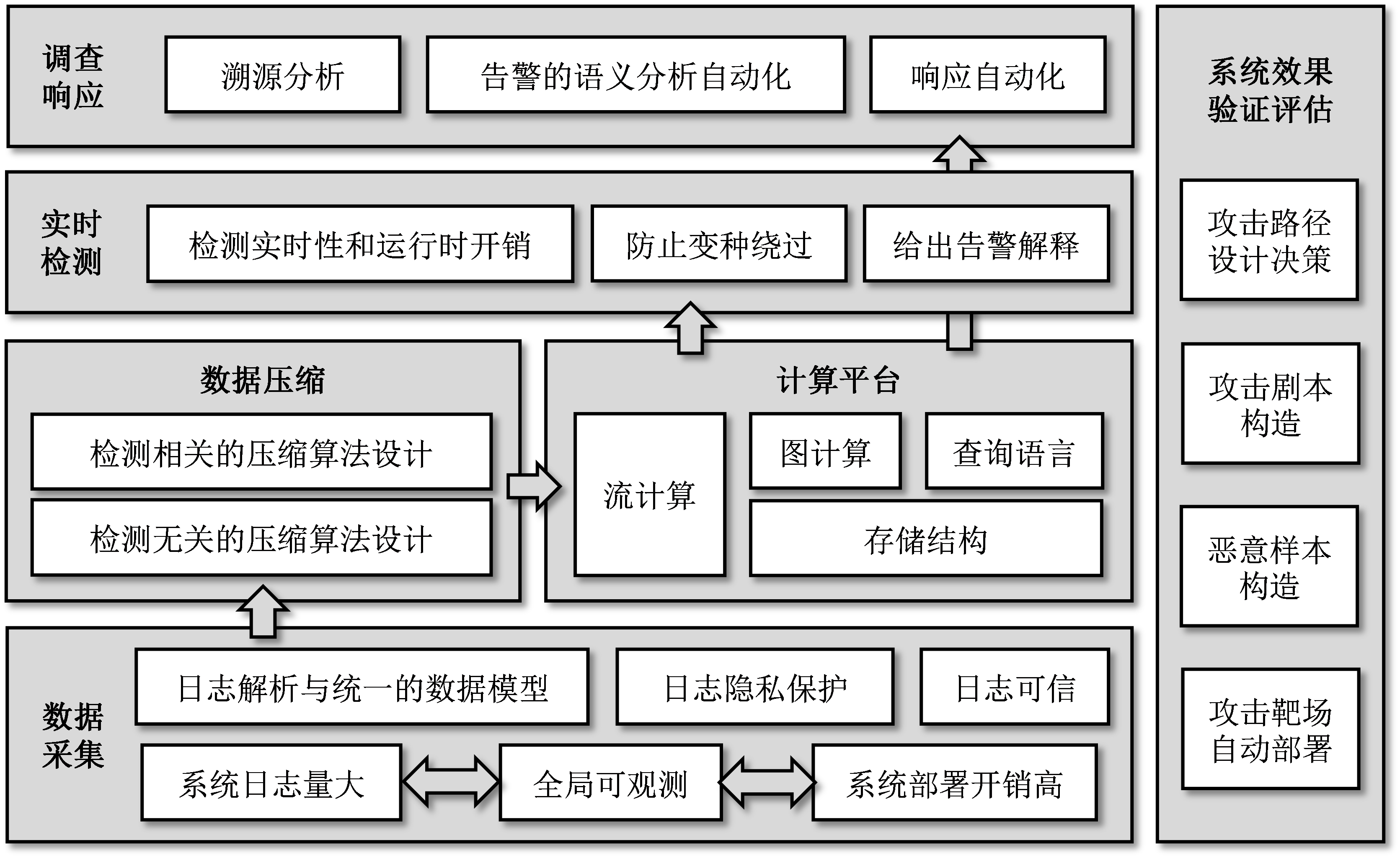
“Learning in Provenance-Based Intrusion Detection: A Survey”
Zhenyuan Li, Yangyang Wei, Zhengkai Wang, Shouling Ji
- The ability of machine learning models to discover and represent features offers new insights and solutions for accurately and efficiently extracting attack patterns, thereby improving the precision of provenance-based detection. Moreover, advances in efficient data compression and indexing enable faster analysis and significantly reduce computational overhead.
[J4] Journal of Cyber Security (in Chinese) “Mobile Spyware and Its Detection: A Survey”, Yi Jiang, Zhenyuan Li#, Fan Zhang, Yixin Jiang, Wenqian Xu, and Zhihong Liang.
[J3] COSE 2025 “AutoSeg: Automatic Micro-segmentation Policy Generation via Configuration Analysis”, Andong Chen, Zhaoxuan Jin, Zhenyuan Li#, Yan Chen, Yu Ning, Ying Wang
[J2] TDSC 2022 “RATScope: Recording and Reconstructing Missing RAT Semantic Behaviors for Forensic Analysis on Windows”, Runqing Yang, Xutong Chen, Haitao Xu, Yueqiang Chen, Chunlin Xiong, Linqi Ruan, Mohammad Kavousl, Zhenyuan Li, Liheng Xu, Yan Chen
[J1] COSE 2021 “Threat Detection and Investigation with System-level Provenance Graphs: A Survey”, Zhenyuan Li, Qi Alfred Chen, Yang Runqing, Yan Chen
[Posters/Workshop Papers]
[W2] PRISM 2026 “Work In Progress: The Case for LLM-Enhanced Backward Tracking”, Jiahui Wang, Xiangmin Shen, Zhengkai Wang, Zhenyuan Li#
[W1] PRISM 2026 “Work In Progress: Building Next-Generation Datasets for Provenance-Based Intrusion Detection”, Qizhi Cai, Lingzhi Wang, Yao Zhu, Zhipeng Chen, Xiangmin Shen, Zhenyuan Li#
[P2] NDSS 2022 “Poster: Towards automated and large-scale cyber attack reconstruction with apt reports”, Zhenyuan Li, Ahmad Soltani, Anis Yusof, Aris Cahyadi Risdianto, Kang Huang, Jun Zeng, Zhenkai Liang, Yan Chen
[P1] ACSAC 2021 “A First Look at Evasion against Provenance Graph-based Threat Detection”, Zhenyuan Li, Runqing Yang, Qi Alfred Chen, Yan Chen
📑 Selected Patents
-
Comprehensive Data Collection: (Patent Application Filed) Fine-Grained Provenance Data Collection Method and Apparatus for Android Systems Based on eBPF (Patent Granted) Fine-Grained Provenance Data Collection Method and System for Cloud Platforms Based on Multi-Layer Data Fusion
-
Efficient Threat Hunting: (Patent Granted) Real-Time Attack Chain Detection Method and System Based on Label Propagation and Event Baseline Learning (Patent Granted) Real-Time Attack Detection Method and System for Streaming Provenance Graphs Based on Labeling and Graph Alignment (Patent Application Filed) Suspicious Event Forward-Backward Tracing and Attack Path Reconstruction Method and System Based on Large Models (Patent Application Filed) Application Risk Assessment Method and Apparatus Based on Large Model Multi-Agent Decision Trees
-
Intelligent Rule Optimization: (Patent Granted) Anomaly Detection Method and System for Streaming Provenance Graphs Based on Iterative Prediction-Correction (Patent Granted) Attack Detection Policy Optimization Method and System Based on Feature Backpropagation
-
Automated Attack Planning: (Patent Application Filed) An End-to-End Network Attack Construction Method (Patent Application Filed) Multi-Stage Automated Penetration Testing Plan Generation Method and System Based on Large Language Models and Attack Tree Models
💫 Selected Fundings
- National Natural Science Foundation of China (Youth Program), Research on Methods and Key Technologies for Large-Scale Real-Time Attack Detection and Attribution, 2024/01-2026/12, Ongoing, PI
- National Key R&D Program of China – “Cyberspace Security Governance” Special Project, Terminal-Oriented Identification, Forensics, and Attribution of Highly Stealthy Propagation-Based Cyber Nuisances, , Ongoing, Sub-Task Leader
- Zhejiang Provincial Key R&D Program (“Leading Goose”), ******, 2025/01-2025/12, Ongoing, PI
- Zhejiang Provincial Key R&D Program (“Leading Goose”), ******, 2024/01-2024/12, Ongoing, Task Leader
- Ningbo “Yongjiang” Young Innovative Talents Project, ******, 2025/01-2027/12, Ongoing, PI
- Natural Science Foundation of Ningbo – Young Doctoral Innovation Research Project, Behavior Governance and Security Protection for Emerging Heterogeneous Systems in Critical Infrastructure, 2026/01-2027/12, Ongoing, PI
- CCF-Tencent “Rhino Bird” Research Fund, Efficient, Intelligent, and Adversary-Aware Attribution Analysis and Threat Hunting, 2026/01-2026/12, Ongoing, PI
- CF-NSFOCUS “Kunpeng” Research Fund, Large-Scale Attribution Analysis Based on Stream Processing in Cloud Computing Environments, 2024/01-2024/12, Completed, PI
- Joint Fund of the National Natural Science Foundation of China, Intelligent Detection and Attribution Methods and Key Technologies for APT Cyber Kill Chains, 2021/01-2023/12, Completed, Core Technical Member
📝 Teaching
- Intelligent Software Quality Assurance (Autumn 2024, Autumn 2025)
🎓 Students
- Undergraduate: Chun Xu (UESTC)
- 2026: Junjie Cheng, Yijie Xu
- 2025: Shiyu Tan (1 * Patent, 1 * Competition Award), Yaokun Li, Qizhi Cai, Haocheng Li, Zhipeng Chen
- 2024: Yuqiao Gu (Ph.D Student, 1 * Patent, 1 * Competition Award), Zhenkai Wang (TDSC Co-1st Author, ACNS 4th Author, Chinese Journal of Computers 3rd Author, 1 * Competition Award), Yi Jiang (Journal of Cybersecurity (Chinese) 1st Author, ACNS 3nd Author, 1 * Competition Award)
- 2023: Jiahui Wang (APSEC’24 2nd Author, ICSE’26 5th Author, 1 * Patent), Mingxiang Shi (1 * Patent), Yangyang Wei (ICML’25 3rd Author, Chinese Journal of Computers 2nd Author, 3 * Patents, 1 * Competition Award), Yu Yang (ICSE’26 1st Author), Yao Zhu (ICML’25 1st Author)
- Alumni: None.
🎖 Honors and Awards
- 2025.12, First Prize of Science and Technology Progress Award by China General Chamber of Commerce (ranked 5/15)
- 2025.09, Second Prize of Science and Technology Progress Award by Beijing Municipal (ranked 7/10)
- 2025.05, National Second Prize and Outstanding Faculty Advisor Award in the Software Innovation Competition (Software System Security Track)
- 2025.03, Research Contribution Award, School of Software Technology
- 2024.09, Ningbo “YongJiang” Talent Programme (Youth Program)
- 2023.03, Huawei’s “Star of Tomorrow”
- 2021.02, Zhejiang Lab’s International Talent Fund for Young Professionals
- 2020.12, Zhejiang University’s Academic Rising Star
- 2020.10, China Scholarship Council (CSC) Joint Ph.D. Program (NUS)
- 2017.05, Outstanding Graduate of Xidian University (Top 1%)
- 2015.11, National Scholarship (Undergraduate) (Top 1%)
💬 Invited Talks
- 2020.10, InForSec Cyber Security Academic Papers Sharing (Co-located with Beijing Cyber Security Conference) | [video]
- 2019.11, Effective and Light-Weight Deobfuscation and Semantic-Aware Attack Detection for PowerShell Scripts, CCS’19, London
🛎️ Academic Service
- TPC Member: IEEE GlobeCom CISS (2026, 2025)
- Editorial Board Member: Digital Twins and Applications(2025-2027)
- Reviewer: TIFS (2026, 2025), TDSC (2025, 2024), TBD (2025) EMSE (2025), TOSEM (2024), Computer & Security (2024), CAAI-TIT (2025), TII (2025), Chinese Journal of Computers (2025, 2024), Journal of Cybersecurity (Chinese) (2024), Computer Science (2024)
- Subreviewer/External reviewer: IEEE S&P (2025, 2024), NDSS (2026, 2022), AsiaCCS (2021), CCS (2019, 2018), ICDC (2019), ESORICS (2019)
📖 Educations
- 2017.09 - 2022.06, Ph.D. in Cyber Security, Zhejiang University, Advised by Prof. Yan Chen.
- 2021.05 - 2022.04, Visiting Ph.D. Student, National University of Singapore, Advised by Prof. Zhenkai Liang.
- 2015.09 - 2019.06, B.S. in Information Security, Xidian University.
- 2010.09 - 2013.06, Zhenhai Middle School, Ningbo.
💻 Working Experience
- 2023.07 - now, School of Software Technology, Zhejiang University, Ningbo/Hangzhou, China.
- 2022.07 - 2023.07, Huawei, 2012 Lab, Hangzhou, China.


